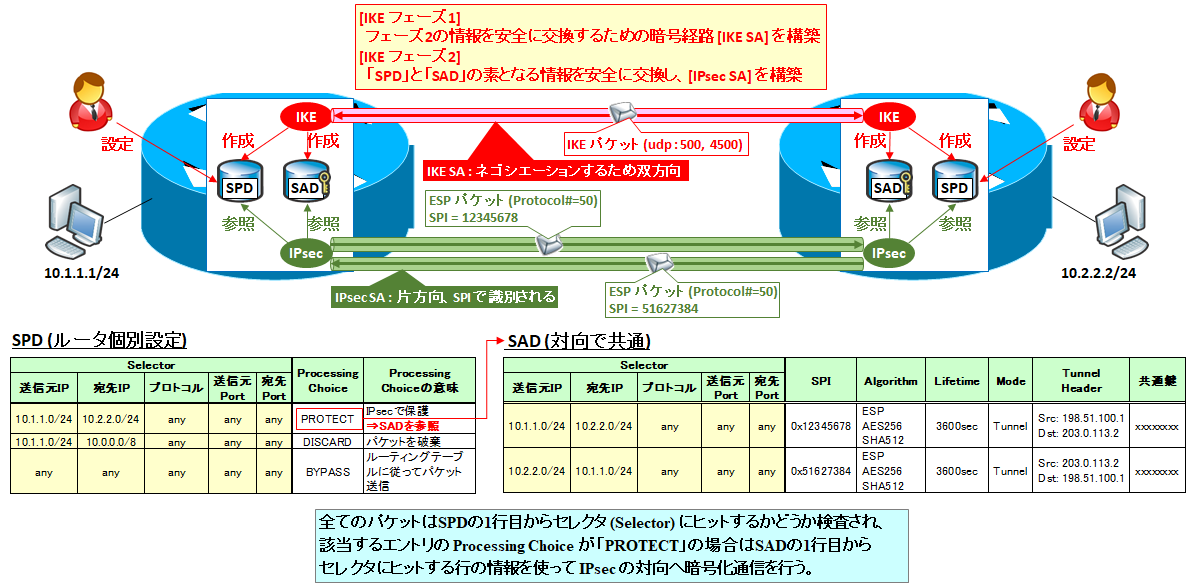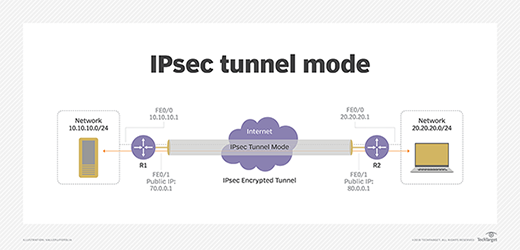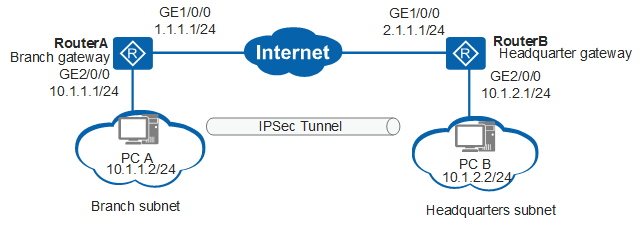
Example for Establishing an IPSec Tunnel in IKE Negotiation Mode Using Default Settings - AR650, AR1600, and AR6100 V300R003 CLI-based Configuration Guide - VPN - Huawei

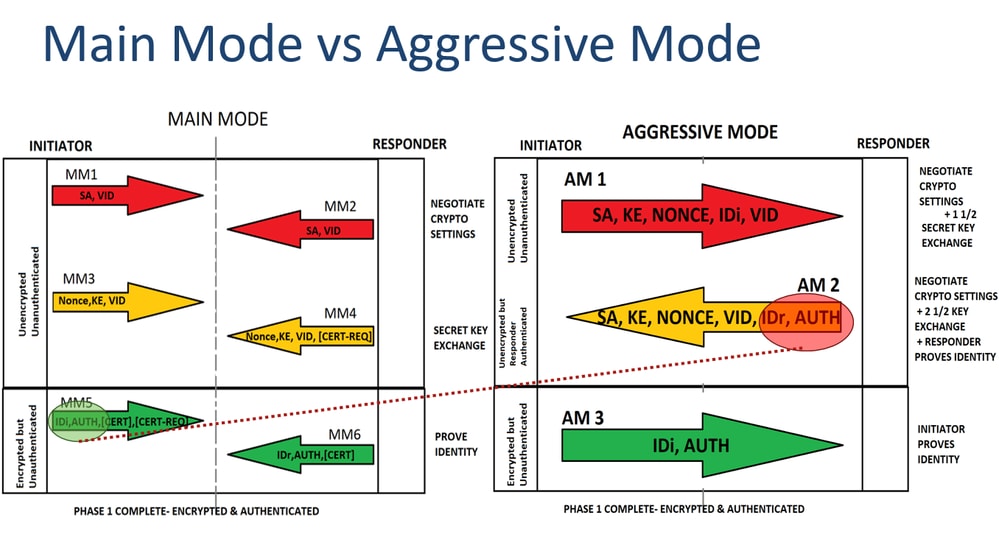
APNIC on Twitter: "There are some differences in setting up an IPsec VPN when using different versions of the Internet Key Exchange (IKE). Our latest #howto covers setting up a #VPN for

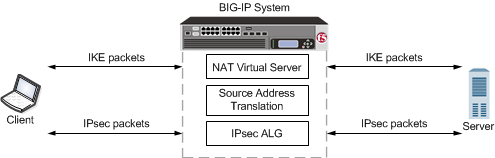
Configure IPsec/IKE site-to-site VPN connections in Azure Stack Hub - Azure Stack Hub | Microsoft Learn

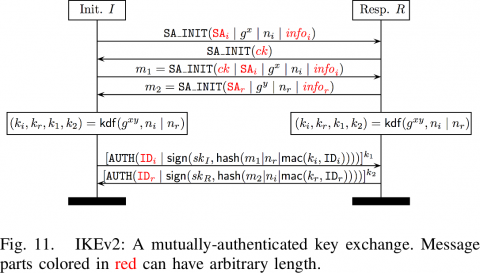
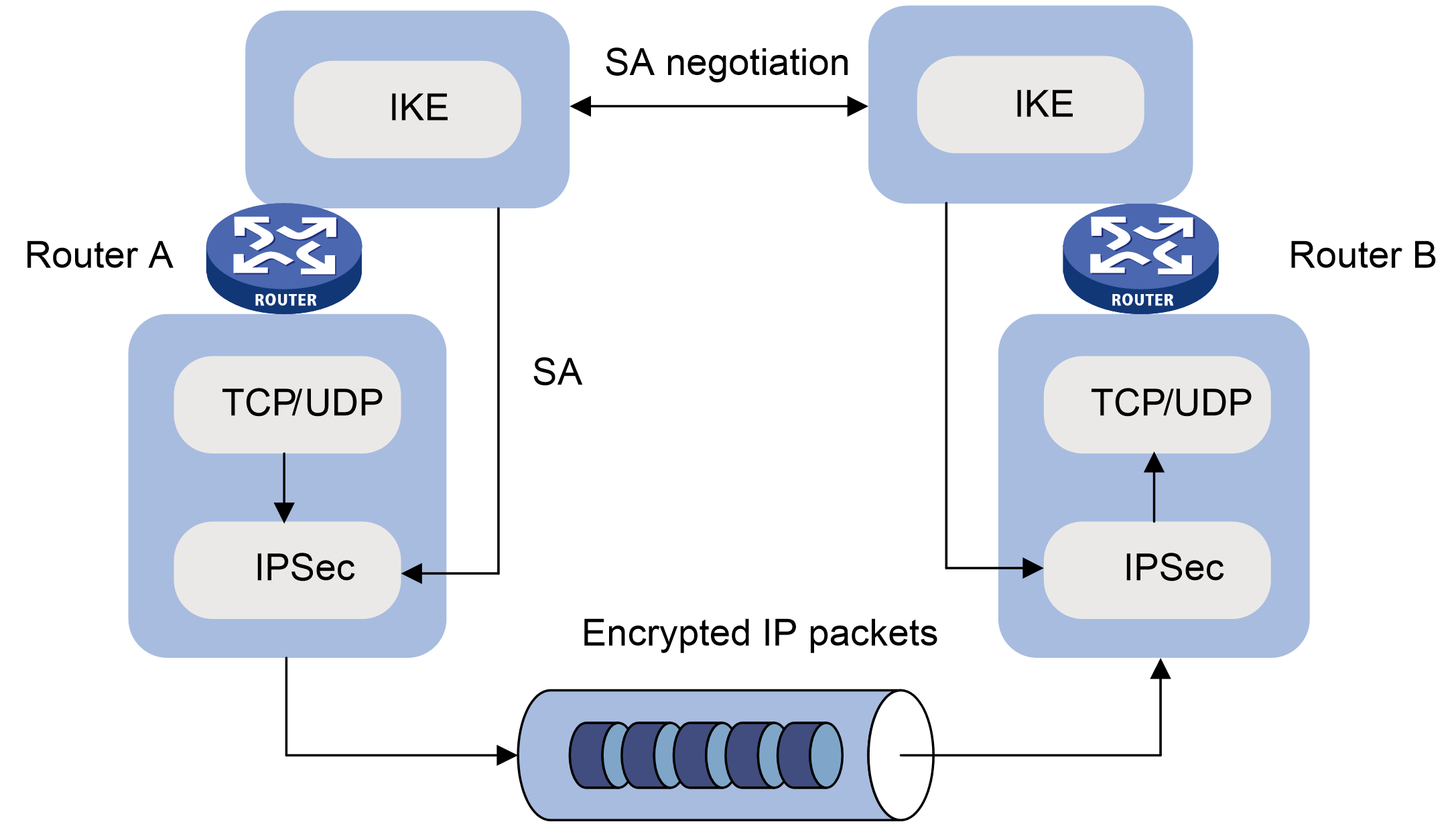
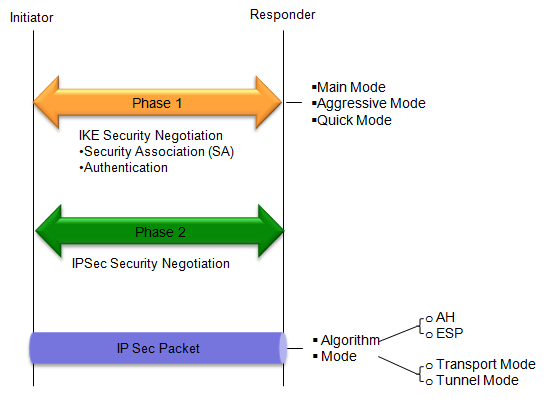
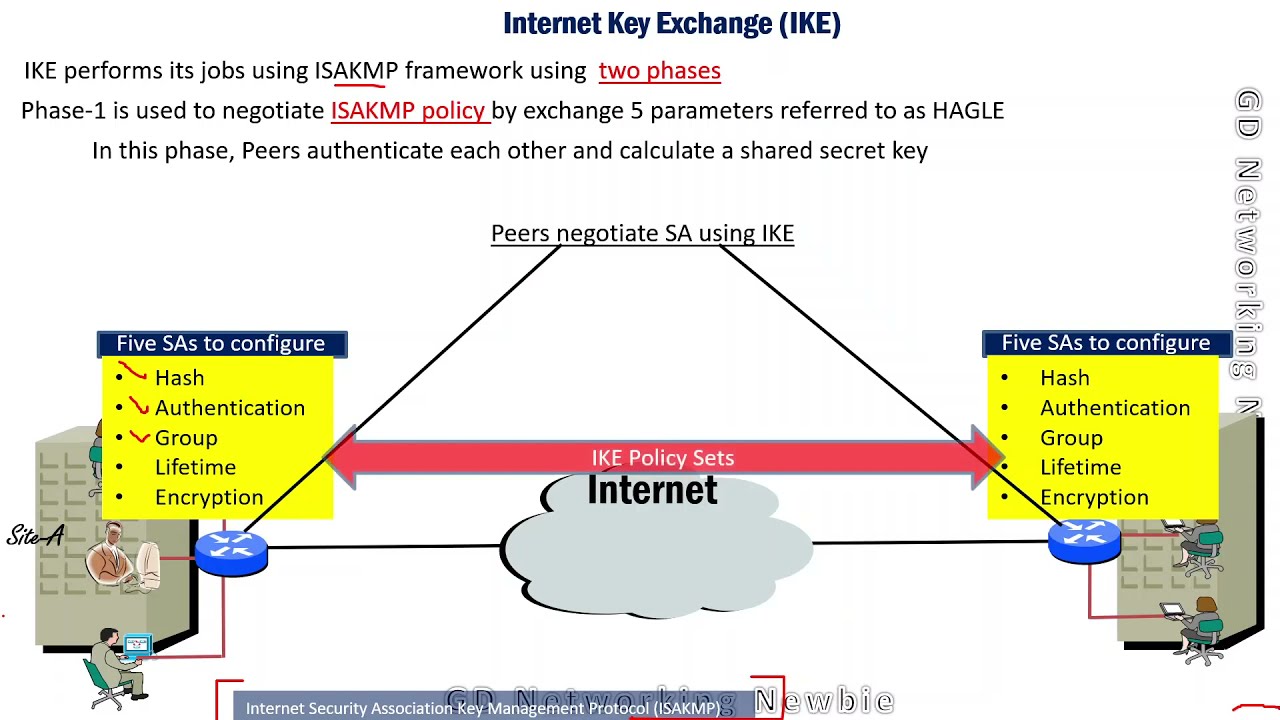
Internet Key Exchange (IKE) and Security Association (SA) by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu